Homelab Raspberry Pi Kubernetes Cluster Current State
Posted on by Josh Kasuboski · 2min read
The cluster is alive and well and exposed to the internet 😱
In a previous post, I put out my plan for the cluster. I mostly followed along, but did end up getting this switch and these ethernet cables.
I ended up with this set-up which is described in more detail below.
Hardware and Monitoring
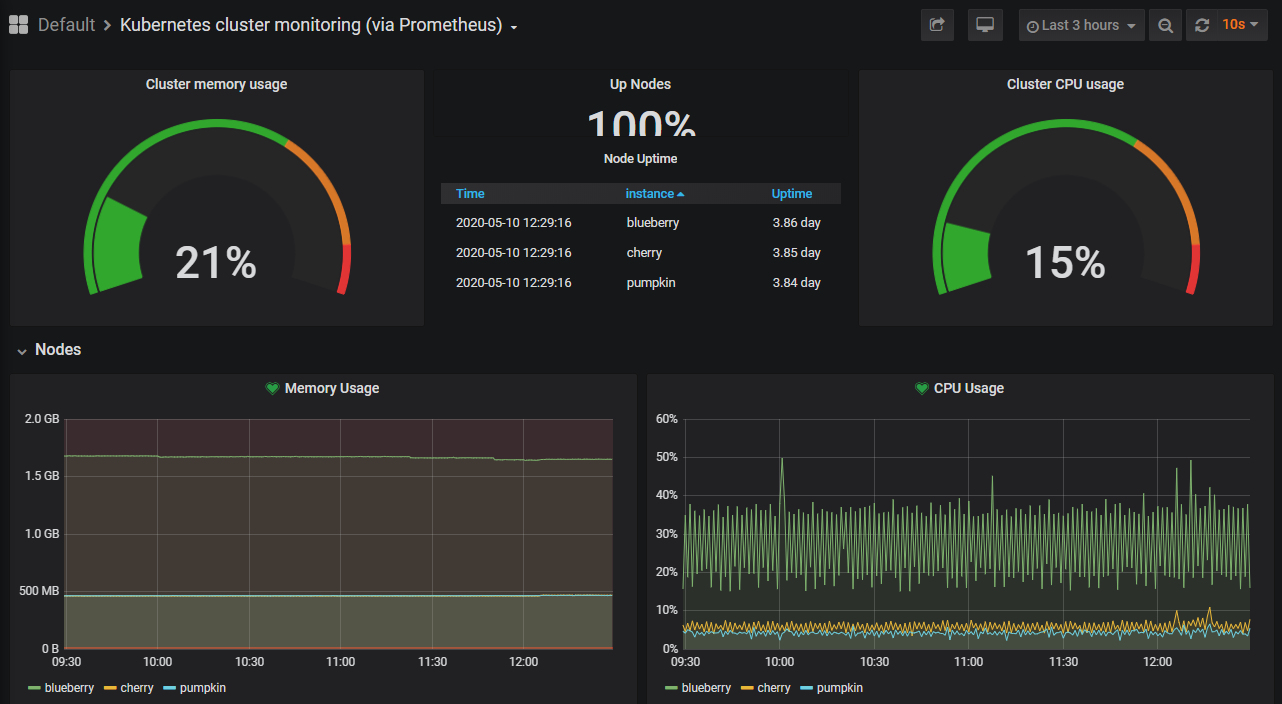
The cluster is set up with Raspbian Lite on 3 Raspberry Pi 4 4gb boards. Raspbian Lite seems to not support 64bit (yet) so I may be changing the operating system. The cluster has the monitoring stack from carlosedp’s repo. I changed some things (mainly the ingress) in my forked repo.
This deploys some nice Grafana dashboards to see the state of the cluster as seen below. blueberry is the master node so hovers around 768m cpu cores and 1285Mi memory usage.
Ingress
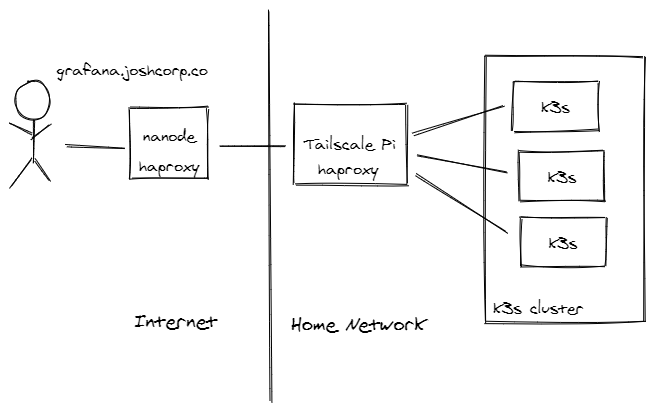
This dashboard is exposed outside the cluster using ingress-nginx with NodePorts. These nodeports are load balanced by an haproxy running in a container on my existing Raspberry Pi 3B+. This is a single point of failure for ingress 😰, but should be good enough for now.
The Ingress is secured using vouch-proxy with the ingress-nginx auth annotations. It uses the IndieAuth backend so I can login using this site as an identity.
Expose to the world
The final piece of the puzzle to expose cluster services to the internet is a Linode nanode. I chose Linode largely because I had a credit… It’s really just providing a public ip address that can forward to my network. I didn’t set up port forwarding to my network instead the haproxy Raspberry Pi and the Linode VM are running tailscale.
Tailscale allows the nanode to connect to my Raspberry Pi with a WireGuard connection through my crazy NAT situation. The nanode is also running an haproxy on ports 80 and 443 on the public ip interface and then proxying that to the tailscale ip of the Raspberry Pi.
I changed the DNS of *.joshcorp.co to point to the nanode. Now that *.joshcorp.co resolves to my cluster on the internet, I can easily use cert-manager to get a certificate from LetsEncrypt.
After all of that, I can access grafana.joshcorp.co outside of my network while authenticating using www.joshkasuboski.com.
What’s Next
I’m pretty happy with the current state. My next move will be making sure everything is tracked in git and can be reproduced. From there I can start deploying.